What are checksums and why do you need them?
Checksums are critically important if you want to make sure the data you have downloaded hasn't been corrupted or tampered with. Checksums are created by hash algorithms like SHA256 or MD5 directly from a file you want to verify. All you need to know about hashes is that given the exact same file, they will reproduce the exact same string of characters. If you change one character in the file the hash will be completely different. This is shown in the example below.
[root@desktop]# echo "I love checksums." | md5sum
26d1fe18b4d5414232e6707acdfc5d3b -
[root@desktop]# echo "I love checksums" | md5sum
062753536863028865f43f4fe6e13719 -
Checksums even work on look-alikes. In the example below, I have changed the "o" in "loves" to the look-alike "о".
[user@desktop# echo "Everyone loves checksums" | md5sum
9b3a59a06b590390167ae1dcecdb9381 -
[user@desktop]# echo "Everyone lоves checksums" | md5sum
0600be673d633072ab7fb6c223eb27d3 -
What are the common utilities and hash algorithms used?
The most common hashing algorithms used in checksums are MD5 and SHA256. You will know the difference between the hashes by the number of characters. MD5 hashes are 32 characters long. A SHA256 hash will produce a 64-character long hash. If available, use the SHA256 hash as it is a more secure algorithm than MD5.
Generally, most systems on Linux will have "sha256sum" and "md5sum" installed by default. Another great utility is gtkhash, although you do have to install it on your Linux machine yourself. Here is a good tutorial about checksums on windows.
Checking Checksums
When downloading a file, generally they will have a checksum page near the download area. This is shown on the VirtualBox website below.
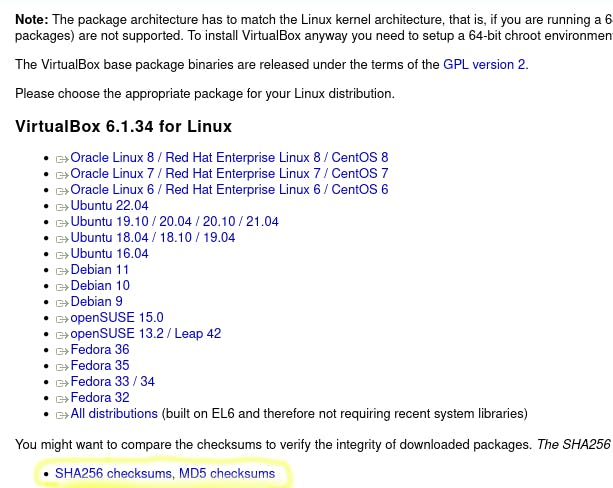
You would then grab the line for the specific file you have.
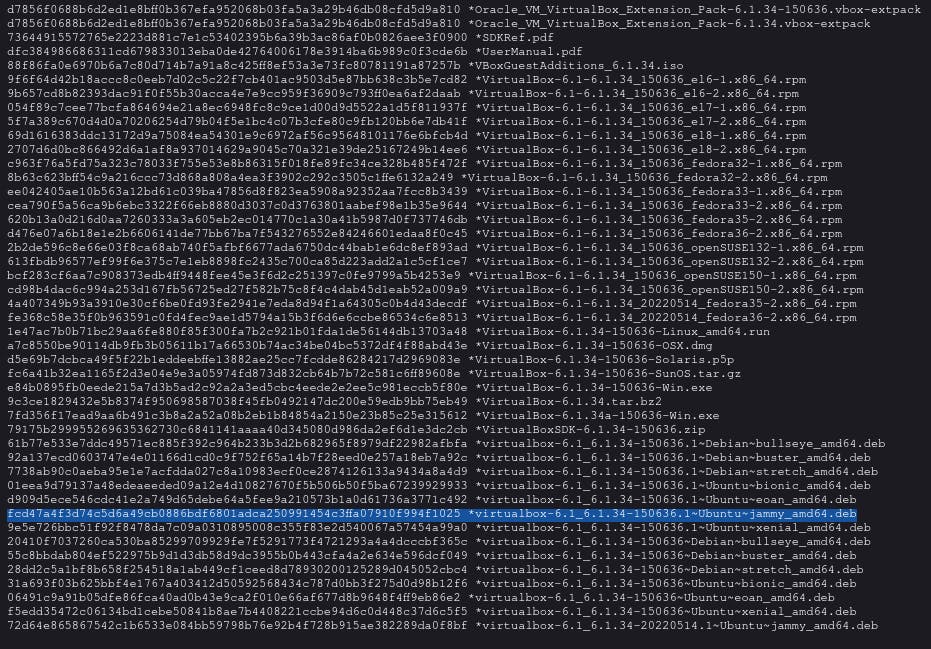
You then put this text into a file in the same directory as your download. In this case, my file name was sum.sha256.
After that, you now need to run sha256sum -c sum.sha256. The -c flag reads from the hash file and checks the download.
[user@desktop]$ nano sum.sha256
[user@desktop]$ sha256sum -c sum.sha256
virtualbox-6.1_6.1.34-150636.1~Ubuntu~jammy_amd64.deb: OK
It outputs that the file has not been corrupted or tampered with.
No matter whether you have an MD5 or SHA512, the commands will be very similar. All you need to switch out is the sha256sum command with md5sum or sha512sum command.
Generating Checksums
Generating checksums is even easier. All you have to do is run this command below:
[user@desktop]$ md5sum file.txt > sum.md5
When we look in the file, it has the same syntax as before.
[user@desktop]$ cat sum.md5
129f303eeb2cea1f29a7bce8b04b18d5 file.txt
Closing Notes
Checksums are invaluable for your security. They are a quick and easy way to keep you safe. Whenever you have a chance to use checksums, use them!


