What is Nmap?
Nmap, short for Network Mapper, is one of the most commonly used ethical hacking tools used to scan for any information about networks; like open ports, open services and basic vulnerability searching. When it comes to hacking into networks, knowledge is power. Nmap gives you a lot of it. It is also a very popular program due to its ease of use and clean installation along with its standalone scripts.
When you have been given an IP of a network you need to know what services are running on the machine. You thus, need to know which ports are open to connect to that service. Ports are necessary for making multiple network requests or having multiple services available. But there are 65,535 ports on any given machine. This is when Nmap comes in. The main uses of Nmap according to their official page is:
- Open ports and services
- Discover services along with their versions
- Guess the operating system running on a target machine
- Get accurate packet routes till the target machine
- Monitoring hosts
Scan types
TCP Connect Scans (-sT)
For anyone that doesn't know what the TCP protocol is, it is a connection-based protocol. In basic terms, before you send any data between two devices you first must make a stable connection. To form this connection, you must do something called a "three-way handshake".
When you first make a connection to a server, you must first send an SYN flag. The server will then acknowledge this packet and respond with an SYN/ACK flag. Finally, our computer will reply with an ACK flag. Now you communicate whatever you want to. In plain English, it sounds like this.
- BROWSER: "Hey server let's talk about something".
- SERVER: "Hey browser, I'm listening to you? What do you want".
- BROWSER: "Okay! I'll tell you now".
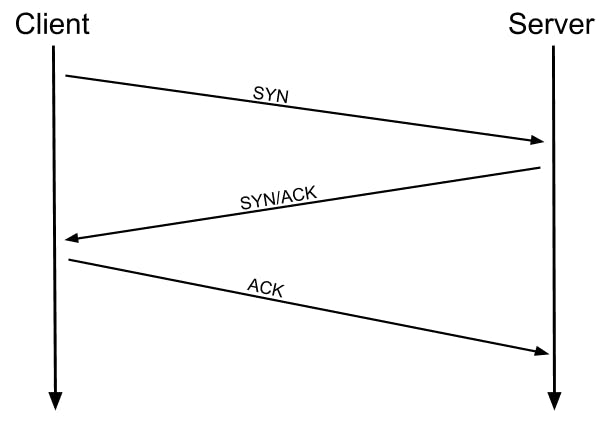
This type of scan is slower and is generally easier to be detected by intrusion detection systems. This scan is the default without root access scan type.
SYN Scans (-sS)
The SYN scan commonly referred to as "Half-open" scans, or "Stealth" scans, is similar to the TCP but it does not complete the full "three-way handshake".
The first two parts of the TCP and SYN scan are the exact same. You first send a SYN flag. The server will then acknowledge this connection and send back an SYN/ACK flag. This is when it differs. Now you send an RST back. An RST flag means this connection should be immediately terminated.
- BROWSER: "Hey server let's talk about something".
- SERVER: "Hey browser, I'm listening to you? What do you want".
- BROWSER: "You should terminate this conversation".
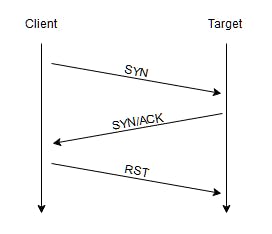
This is more of a "stealthy" scan than the TCP scan and will fool old intrusion detection systems. This scan requires root permission as it needs to be able to create raw packets, this is reserved for root users.
UDP Scans (-sU)
UDP is a stateless protocol. What this means is, that it doesn't do a back-and-forth handshake like TCP. UDP connections rely on sending packets to a target port and hoping that they make it and none of them goes missing. While this is helpful for connections that aim for speed over quality it is not the best for scanning ports due to the lack of acknowledgment. This makes UDP harder and much slower to scan.
Useful switches
OS Scanning (-O)
Nmap can also provide information about the operating system using TCP/IP fingerprinting. This is also enabled by default with the aggressive switch (-A).
Service and Version Detection (-sV)
Enables version detection.
Aggressive scanning (-A)
Aggressive scanning enables Os detection, version detection, script scanning, and traceroute.
Timing (-T<0-5>)
The switch -T sets timing and aggressiveness (higher is faster). -T5 would be an incredibly fast scan that assumes you are on an extremely fast and reliable network. -T0 would be for evading intrusion detection system. This scan would be an incredibly long time and would not give too much information.
Port Scanning (-p)
By default, if you don't have this flag you will scan the top 1000 common ports.
- To specify a port just add it in after with ```-p````.
> nmap -p 973 [MACHINE IP]
- To specify multiple ports add a comma.
nmap -sV -p 22,53,110,143,4564 198.116.0-255.1-12 [MACHINE IP]
- To scan between a range add a hyphen between two numbers.
nmap -p 76–973 [MACHINE IP]
- This will scan all 65,535 ports.
> nmap -p- [MACHINE IP]
- Use the
--top-portsflag to specify the top n ports.
> nmap --top-ports 10 scanme.nmap.org
NSE Scripts (-sC)
I will not get too much into this but if you use -sC to scan ports, then it will scan with default NSE scripts that are considered useful for discovery.
Examples of Nmap scans
If I want a quick and dirty scan on a network to find the service, Os and basic open ports.
nmap -sC -sV -T4 [MACHINE IP]
If you want to launch a stealth scan on a network and try to determine the Operating System and services.
nmap -sV -p 22,53,110,143,4564 198.116.0-255.1-127
If you want to launch a TCP scan on a machine.
nmap -sT -p 22,53,110,143,4564 198.116.231.43
Closing notes
Nmap is an incredibly useful program for anyone who deals with networks daily. I am barely showing you the top of the iceberg. There is a full dedicated scripting engine, quite a few more types of scans and hundreds of other options. I highly recommend NMAP
I recommend you check out the documentation of Nmap here.

